
Cybersecurity Strategy and Imperatives: A Guide for Business Leaders
A cybersecurity strategy isn’t just a safeguard—it’s the backbone of modern business resilience. Cyber threats don’t knock before they strike, and organizations that wait to react often suffer irreversible damage. The question isn’t if an attack will happen, but when—and how prepared your business will be when it does.
The global cybersecurity managed services market is expected to reach $32.68 billion by 2030, growing at an 11.0% CAGR. This surge underscores a stark reality: businesses are investing heavily in security because cyber risks are no longer an afterthought—they’re a boardroom priority.
Leaders who fail to prioritize cybersecurity today risk falling behind in both security and trust.Chris Butler, executive VP at IP Services, says, “A strong cybersecurity posture isn’t about eliminating risk—it’s about controlling it before it controls you.”
The key to staying ahead is a proactive, leadership-driven approach that integrates security into every aspect of your organization. The VisibleOps Cybersecurity methodology provides a structured approach to strengthening security at every level.
In this blog, we’ll break down six essential steps every business leader must take to strengthen their cybersecurity framework.
Cybersecurity Strategy Begins at the Top: Lead with a Security-First Mindset
A strong cybersecurity strategy starts with leadership. CXOs and senior executives must champion a security-first culture, ensuring that cybersecurity is woven into every business decision. When leadership prioritizes security, the entire organization follows.
This is more urgent than ever—43% of all data breaches target SMBs, yet many businesses still underestimate their risk. Leaders who fail to embed cybersecurity into their operations leave their organizations vulnerable to costly attacks and reputational damage.
By setting the tone from the top, business leaders can drive company-wide awareness, accountability, and resilience. A well-defined cyber risk management approach ensures that security becomes second nature—not just an afterthought.
Staying Ahead of Cyber Threats: Proactive Defense for Long-Term Security
A strong cybersecurity strategy demands real-time insights to combat ever-evolving cyber threats. Without the right expertise or tools, businesses leave themselves exposed to attacks that could have been prevented. Partnering with a cybersecurity service provider ensures continuous monitoring and rapid response, closing critical security gaps.
♦ Cyber threats don’t wait—your defenses shouldn’t either. A reactive approach leaves businesses vulnerable. Proactive cyber risk management ensures threats are identified and mitigated before they escalate.
♦ Not every business has an in-house security team—and that’s okay. Partnering with a cybersecurity service provider helps fill the gaps, offering continuous monitoring and expert support.
♦ Threat intelligence is more than just data—it’s about actionable insights. Businesses need real-time analysis to detect attack patterns, predict threats, and take preemptive action.
♦ Cybersecurity best practices evolve, and so should your strategy. Cybercriminals adapt quickly; staying ahead requires regular updates, ongoing assessments, and a mindset that treats cybersecurity as a long-term investment.
By integrating cyber risk management into everyday operations, businesses strengthen their defenses, reduce exposure, and ensure continuity in an increasingly hostile digital landscape.
Cybersecurity Best Practices: Deploying Advanced Threat Hunt Technologies
A rock-solid cybersecurity strategy doesn’t rely on luck—it’s built on cybersecurity best practices that anticipate threats before they strike. AI-powered threat hunt tools and technologies act as your organization’s digital watchdogs, scanning for vulnerabilities and responding to risks in real time.
But here’s the catch: even the best technology is useless if it’s not properly deployed.
If your IT team is stretched thin or lacks expertise, bringing in cybersecurity specialists can make the difference between a near-miss and a full-blown data breach. Effective cyber risk management isn’t just about having the right tools—it’s about using them wisely.
When businesses integrate these solutions into daily operations, they shrink attack surfaces, reduce false positives, and keep cybercriminals guessing.
Cyber Threat Readiness: Outsmarting Phishers & Mitigating Inevitable Attacks
Even the most advanced security infrastructure can’t counteract human fallibility. All it takes is a single misstep—one deceptive email, one compromised credential—to open the floodgates to a full-scale breach. Cyber resilience isn’t just about risk management; it’s about proactive defense in a threat landscape where an attack isn’t a possibility—it’s inevitable.
♦ Phishing attacks aren’t just annoying—they’re a business killer. In fact, small businesses are 350% more likely to fall victim to phishing than large enterprises. Why? Because attackers know smaller organizations often lack the same security awareness training and resources.
♦ Passwords should never serve as a weak link in the security chain. Credential stuffing and brute-force attacks thrive on predictable, recycled passwords. Establishing robust, randomized, and frequently updated credentials isn’t just Cybersecurity 101—it’s an absolute requirement.
♦ One click can dismantle an entire system. Malicious payloads embedded in phishing emails exploit cognitive biases, urgency tactics, and social engineering. Employees must be trained to dissect sender information, scrutinize URLs, and report anomalies before irreversible damage occurs.
♦ Cybersecurity training must be dynamic, immersive, and relentless. Static, one-time training modules are ineffective against ever-evolving attack methodologies. Continuous education, simulated breaches, and real-time response drills ensure employees remain an active, adaptive component of your security posture.
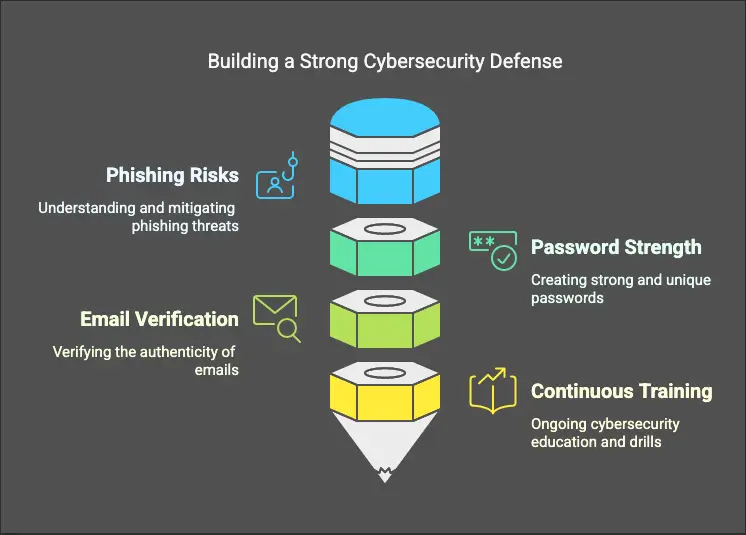
At the end of the day, your cybersecurity posture is only as strong as the people who uphold it. Give your team the knowledge they need, and they’ll become your first line of defense—rather than your biggest vulnerability.
The Role of Penetration Testing & Compliance Audits
Testing your network, systems, and software for vulnerabilities isn’t optional—it’s essential. Regular penetration testing (PEN testing) identifies weak points before attackers do, giving businesses the opportunity to fix security gaps proactively. But testing alone isn’t enough. Maintaining compliance with industry regulations is just as critical.
That’s where Compliance as a Service (CaaS) comes in. It ensures that your organization doesn’t just check regulatory boxes but actively strengthens its security posture. A well-structured cybersecurity strategy integrates both penetration testing and compliance audits, creating a security-first approach that mitigates risk, prevents costly fines, and builds customer trust.
Cybersecurity Best Practices: Managing IT Assets & Securing Your Attack Surface
If you don’t know what’s in your IT environment, how can you protect it? A well-defined cybersecurity strategy starts with securing every asset before attackers find an opening.
A cyber risk management approach that includes cybersecurity best practices for IT asset inventory ensures businesses maintain control over their digital landscape, reducing exposure and reinforcing resilience.
♦ Asset visibility is everything. Businesses need a comprehensive IT inventory to track hardware, software, and cloud environments—because you can’t protect what you don’t know exists.
♦ Unsecured devices create easy entry points. Shadow IT, outdated systems, and misconfigured assets expand the attack surface. Identifying and securing these risks should be a top priority.
♦ Attack surfaces must shrink, not expand. Without regular monitoring, organizations accumulate vulnerabilities. Routine security assessments ensure that every endpoint, server, and cloud application remains protected.
♦ IT processes should evolve alongside threats. Cybercriminals adapt quickly—your asset management and security practices must do the same. Staying ahead means continuous updates, real-time tracking, and swift action when weaknesses are detected.
Cybersecurity as a Continuous Business Imperative With IP Services
Cybersecurity isn’t a box to check—it’s a continuous commitment. Threats evolve, attack methods change and businesses that stand still quickly become vulnerable. Implementing these six cybersecurity best practices ensures that security becomes an ongoing process, not just an afterthought.
A resilient cybersecurity strategy protects more than just data—it safeguards operations, reputation, and financial stability. It starts at the top, with leadership driving a security-first culture, and extends to every employee, system, and process.
| Explore our range of IT Services in Salem: | |
| Managed IT | IT Consulting |
| Cybersecurity | IT Support |
Start reinforcing your defenses today—because in cybersecurity, waiting until tomorrow is already too late.


