
The Hidden Dangers of Security Misconfiguration
80% of security incidents stem from misconfigured settings, making it one of the biggest threats to businesses today. Cybercriminals don’t always need sophisticated tools to break into systems.
Sometimes, a simple security misconfiguration provides an easy entry point. Open databases to weak passwords; these vulnerabilities expose businesses to cyberattacks, compliance failures, and financial losses.
Chris Butler, executive VP at IP Services, says, “Security is not just about stopping attacks. It’s about eliminating the loopholes that invite them in the first place.”
If your organization neglects secure configurations, you are handing cybercriminals an open door. This blog will help you identify and prevent security misconfiguration attacks before they lead to costly breaches.
What is a Security Misconfiguration and Why Does It Happen?
A security misconfiguration happens when system settings are left insecure, making them vulnerable to cyber threats. These misconfigurations can exist in applications, networks, servers, databases, or cloud environments.
Common causes include:
- Default Settings Left Unchanged: Many devices and applications come with default passwords and open access configurations. If not updated, these settings are easy for hackers to exploit.
- Unpatched Software: Outdated systems often have known security gaps. Attackers target these vulnerabilities to gain unauthorized access.
- Improper Access Controls: Assigning excessive privileges to users or failing to restrict access exposes sensitive data.
- Lack of Security Audits: Without regular security assessments, misconfigurations go unnoticed, making businesses easy targets.
If these gaps exist in your IT environment, attackers can exploit them to steal data, disrupt operations, or even deploy ransomware.
How Security Misconfiguration Creates Vulnerabilities
When systems are misconfigured, they become an easy target for attackers. These security misconfiguration vulnerabilities allow unauthorized access, data leaks, and system takeovers.
Some critical risks include:
- Data Exposure: Open cloud storage, weak encryption, or misconfigured access controls can expose sensitive information to unauthorized users.
- Privilege Escalation Attacks: Poorly managed permissions allow attackers to move from basic access to full control of a system.
- Service Disruptions: Attackers can exploit misconfigurations to shut down critical business systems, leading to downtime and revenue loss.
- Regulatory Non-Compliance: Failing to maintain secure configurations can result in penalties under regulations like GDPR, HIPAA, and PCI-DSS.
Common Security Misconfiguration Examples
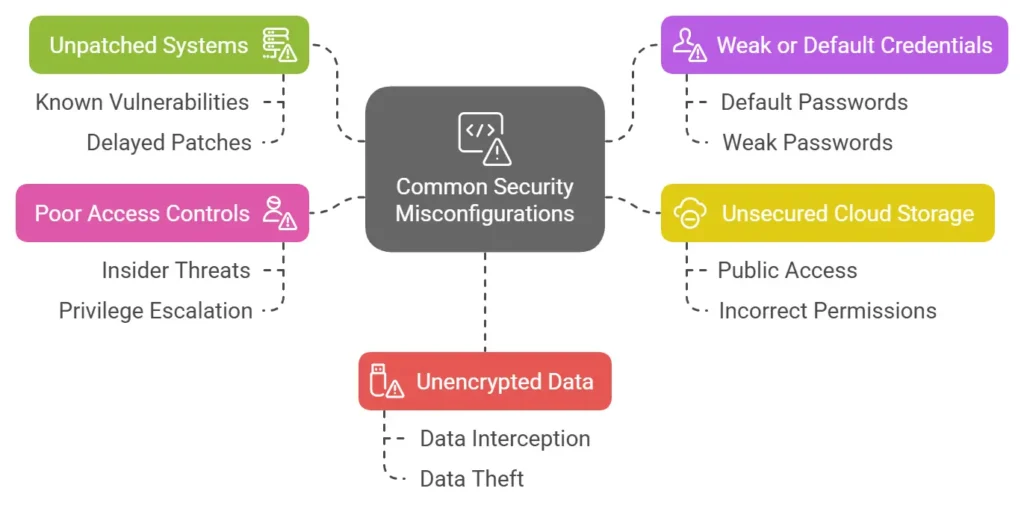
Misconfigurations are among the most common security risks, often caused by oversight or lack of security best practices.
Below are key examples that expose businesses to cyber threats.
Unpatched Systems
Outdated software contains known vulnerabilities that attackers exploit. According to Sophos’ State of Ransomware 2024 report, 32% of cyberattacks stem from unpatched vulnerabilities.
Organizations often delay security patches due to compatibility concerns or lack of IT resources, exposing systems. This increases the risk of ransomware, data theft, and system takeovers.
Weak or Default Credentials
Many organizations fail to change default passwords or use weak login credentials. Attackers use automated tools to guess passwords, gaining access to sensitive systems. Strong, unique passwords and multi-factor authentication (MFA) significantly reduce this risk.
Unsecured Cloud Storage
Publicly accessible cloud storage is a common issue. If cloud permissions are not configured correctly, anyone with an internet connection can access sensitive files. Cloud environments should be regularly audited to ensure proper access restrictions.
Poor Access Controls
Over-permissioned user accounts allow employees or attackers to access critical systems they shouldn’t. This increases the risk of insider threats and privilege escalation attacks. Implementing the principle of least privilege (PoLP) ensures that users only have access to what they need.
Unencrypted Data
Data transmitted or stored without encryption is vulnerable to interception and theft. This is especially risky for businesses handling customer financial or personal information.
Encrypting sensitive data at rest and in transit prevents unauthorized access and data breaches.
How to Prevent Security Misconfiguration Vulnerabilities
Security misconfigurations can be prevented with proactive measures. Here are key steps businesses should take to secure their systems and reduce vulnerabilities.
Regular Patch Management
Keeping software up to date prevents attackers from exploiting known vulnerabilities. Businesses should implement an automated patching system that applies security updates as soon as they become available. Regular vulnerability scans help identify unpatched systems that need attention.
Secure Configuration Practices
Every system should follow a secure baseline configuration. This includes disabling unnecessary services, closing open ports, and enforcing security policies across all devices and applications. Configuration management tools can help enforce security settings and detect deviations in real-time.
Strong Access Controls
Implement role-based access control (RBAC) to ensure users only have the permissions necessary for their job functions. Regularly review and update user permissions to prevent excessive access. Enforce multi-factor authentication (MFA) to add an extra layer of security, reducing the risk of unauthorized access.
Continuous Security Audits
Regular security assessments help detect and fix security misconfiguration vulnerabilities before attackers exploit them. Businesses should use automated scanning tools to identify misconfigurations in firewalls, cloud settings, and application permissions. Internal and external penetration testing also helps uncover weak security settings.
Employee Training
According to CloudSecureTech, external actors cause 65% of breaches, while 35% are attributed to employee errors rather than malicious intent. Training employees on security best practices ensures they understand the importance of strong passwords, recognizing phishing attempts, and following secure cloud usage guidelines. Ongoing cybersecurity awareness programs help prevent common mistakes that lead to security vulnerabilities.
Security Misconfiguration Risks: What the Numbers Say
Security misconfigurations can lead to serious consequences for businesses. Real-world incidents highlight the risks associated with common missteps.
Here’s a breakdown of misconfiguration types, their risk levels, and their potential impact:
| Misconfiguration Type | Risk Level | Real-World Impact |
| Unpatched Systems | High | The 2017 Equifax breach exposed 147 million records due to an unpatched vulnerability. |
| Weak Credentials | Critical | 81% of hacking-related breaches involve stolen or weak passwords. |
| Open Cloud Storage | High | Misconfigured AWS buckets have led to data leaks affecting millions of users. |
| Poor Access Controls | Medium | Excessive permissions can lead to insider threats and privilege escalation attacks. |
| Unencrypted Data | High | Unsecured databases expose sensitive customer and financial information. |
Secure Your Business with IP Services’ All-round Cybersecurity Solutions
Security misconfigurations are preventable. Proactive measures, regular audits, and security best practices keep your business safe from cyber threats.
IP Services specializes in cybersecurity and compliance, helping organizations eliminate security misconfiguration vulnerabilities before they become threats. With over 23 years in business and over 100 years of cybersecurity expertise, we provide enterprise-level security tailored to your needs.
Contact us today to assess your security posture and strengthen your defenses.


