
Understanding Network Vulnerabilities: Identifying and Mitigating Security Threats
In today’s hyperconnected world, network vulnerabilities are an ever-present threat to businesses of all sizes. From misconfigured firewalls to outdated software, weaknesses in a company’s network can leave it exposed to a variety of cyber threats.
Consider this: attackers were able to exfiltrate data in less than a day after compromise in 45% of cases. This startling statistic underscores the critical importance of having robust defenses in place, without which the consequences of a network breach can be devastating—resulting in significant financial losses, reputational damage, and disrupted operations.
As Chris Butler, executive VP at IP Services, notes, “In a world where cyberattacks move faster than many organizations can respond, the real challenge lies in identifying and patching vulnerabilities before they’re exploited. It’s no longer enough to react—businesses must anticipate and prevent these threats.”
In this blog, we’ll dive into the various types of network security vulnerabilities, explore their root causes, and provide actionable steps to safeguard your business from potential cyberattacks.
Understanding Network Security Vulnerabilities
1. Software Vulnerabilities
Software vulnerabilities are among the most common weaknesses exploited by cyber attackers. These can include unpatched operating systems, outdated applications, or bugs within the code.
Hackers target these flaws to gain unauthorized access or control over your network. Organizations often delay updates, creating long windows of exposure for attackers to exploit.
Ensuring regular software updates and patching is critical to closing these gaps, as vulnerabilities left unpatched for extended periods increase risk.
2. Misconfigured Networks
A misconfigured network can inadvertently leave the door wide open to cyber threats.
This often occurs when firewalls, routers, or security settings are not properly set up, allowing unauthorized access. Poor configuration can happen due to oversight or lack of IT expertise, making your network an easy target for hackers. Once inside, attackers can move laterally across systems undetected.
Organizations should conduct regular audits of their network configurations and utilize automated tools to spot misconfigurations before they become security incidents.
3. Insider Threats
Not all vulnerabilities come from outside attacks—insider threats are equally dangerous. Employees, whether intentionally or accidentally, can compromise network security by mishandling sensitive data, falling for phishing scams, or granting unauthorized access.
Insider threats often go undetected, causing long-term damage. The average network dwell time for a persistent threat in an organization with up to 250 employees is 51 days, giving attackers ample time to do damage. Implementing strict access controls, regular training, and monitoring employee activities can help reduce this risk.
4. Weak Passwords and Authentication Protocols
Weak passwords and poor authentication protocols are significant vulnerabilities that attackers can exploit with relative ease. Many organizations fail to enforce strong password policies, leaving their networks exposed to brute-force attacks. Additionally, failing to implement multi-factor authentication (MFA) increases the risk of unauthorized access.
Encouraging employees to use complex passwords, rotating them regularly, and implementing MFA are essential steps to strengthen network security and minimize the risk of credential-based attacks.
5. Lack of Encryption
Failing to encrypt sensitive data, both at rest and in transit, presents a critical vulnerability. Without encryption, attackers who intercept data transmissions or gain access to storage systems can easily view or steal sensitive information. This weakness becomes especially dangerous when dealing with personal data, intellectual property, or financial records.
Organizations should employ encryption standards such as AES-256 to protect data during transfers and when stored on servers or devices, ensuring that even if attackers gain access, the data remains unreadable.
6. Inadequate Endpoint Security
Endpoints like laptops, smartphones, and IoT devices connected to a network often serve as entry points for attackers. Without proper endpoint security measures, such as antivirus software, device monitoring, and endpoint detection and response (EDR) solutions, these devices become vulnerable to malware, ransomware, and other attacks.
Ensuring that all endpoints are secure through regular software updates, device monitoring, and robust antivirus measures will reduce the risk of a successful attack through these devices.
7. Unsecured Remote Access
With the rise of remote work, unsecured remote access has become a significant network vulnerability. Many organizations rely on virtual private networks (VPNs) or remote desktop protocols (RDPs) to allow employees to access the company’s network from outside the office. However, when these tools are not properly secured or updated, they create a backdoor for attackers to exploit.
Organizations should enforce strict remote access policies, ensure that VPNs and RDPs are updated regularly, and implement multi-factor authentication to secure remote connections.
8. Lack of Network Segmentation
Without proper network segmentation, an attacker who gains access to one part of the network can potentially move freely across the entire infrastructure. This lack of separation between systems, devices, and users can allow for a more widespread impact once a vulnerability is exploited, increasing the potential for significant damage.
To mitigate this risk, organizations should segment their networks based on roles, permissions, and the sensitivity of data. This limits access to critical systems, reducing the damage an attacker can cause if they breach one area.
9. Phishing and Social Engineering Attacks
Phishing and social engineering attacks exploit human vulnerabilities rather than technical weaknesses, making them particularly dangerous. Attackers trick employees into revealing sensitive information, downloading malware, or granting unauthorized access, often through deceptive emails or messages.
Organizations should implement regular cybersecurity training programs to educate employees on recognizing phishing attempts and social engineering tactics, as well as enforcing security protocols like email filtering to reduce the likelihood of such attacks.
10. Outdated or Unsupported Hardware
Using outdated or unsupported hardware presents another serious vulnerability. Older devices may lack the necessary security features to protect against modern threats, and manufacturers often stop providing security updates and patches over time. This leaves the hardware exposed to new vulnerabilities that attackers can exploit.
Regularly reviewing hardware, upgrading outdated devices, and ensuring that all systems receive necessary patches and updates can prevent attackers from exploiting these vulnerabilities.
Safeguarding Your Network Against Vulnerabilities
1. Regular Vulnerability Assessments
One of the most effective ways to safeguard your network is through regular vulnerability assessments.
These evaluations help identify and prioritize the most critical weaknesses in your system before they can be exploited. By consistently reviewing your network for potential risks, you can take proactive steps to mitigate them.
Regular assessments also keep your security strategy up to date with evolving threats, ensuring that no vulnerability lingers in your system for years. In fact, 75% of cyberattacks targeted vulnerabilities that had been present for two or more years, a statistic that underscores the importance of timely assessments.
2. Network Monitoring and Threat Detection
Active network monitoring is crucial for detecting and responding to threats in real time. By using automated tools and AI-driven solutions, businesses can continuously monitor their networks for suspicious activity and vulnerabilities.
Early detection of network breaches allows companies to respond quickly and prevent attackers from accessing sensitive data. Real-time monitoring can drastically reduce the time attackers have within your network, helping to minimize damage from persistent threats.
3. Patch Management and System Updates
Consistent patch management is essential to fixing vulnerabilities as soon as they are discovered. In the rush of daily operations, patching is often delayed or overlooked, but this can leave your network exposed to long-standing vulnerabilities.
Implementing automated patch management systems ensures that your network remains protected from known vulnerabilities without interrupting your workflow.
| More articles you might like: |
The High Stakes of Ignoring Network Security
The consequences of a cyberattack can be dire for small businesses. Cloudsecuretech reports that 60% of small companies hit by a cyberattack go out of business within six months. This underscores just how critical it is to take network security seriously.
A single breach can lead to overwhelming financial loss, loss of customer trust, and business closure. By addressing vulnerabilities now, you can protect your business from these devastating outcomes.
Here is a brief look at some common vulnerabilities, the risks they pose, and actionable preventive measures to reduce these risks.
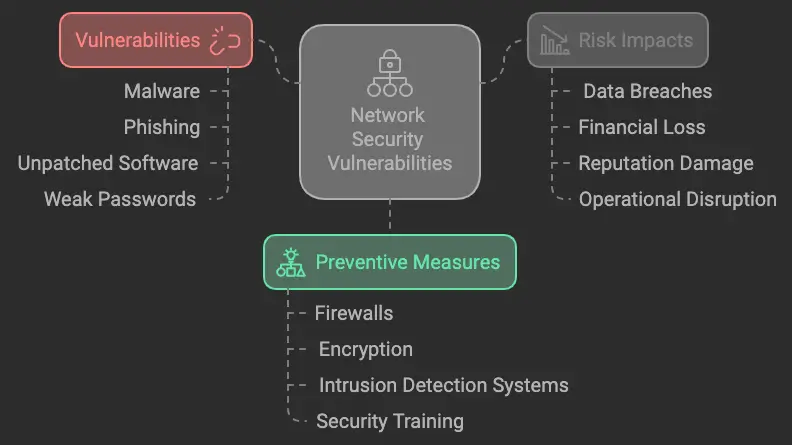
By addressing these vulnerabilities with the appropriate measures, you can significantly reduce the likelihood of a cyberattack and protect your business from potentially devastating consequences. Being proactive in network security is key to long-term success and stability.
Strengthen Your Network Security with IP Services
When you partner with us, you’re not just getting a service provider—you’re gaining a security ally. We specialize in staying one step ahead of cyber threats with tailored, proactive solutions that safeguard your network from every angle.
From rapid detection and response to continuous monitoring and expert guidance, we’re committed to fortifying your business against vulnerabilities.
Contact us to minimize risk and ensure your business thrives in today’s digital landscape.


