
Crafting an Effective Network Security Plan for Your Business
A well-crafted network security plan is essential for organizations to safeguard data and maintain operational continuity in today’s threat-laden digital world. For any business handling sensitive information, a security strategy isn’t just beneficial—it’s essential to protect assets and build trust.
A recent survey found that 16% of organizations suffered losses exceeding $1 million due to information security incidents. This statistic underscores the financial risks of cyber vulnerabilities, highlighting the urgent need for proactive security measures to protect against potential losses and damage to reputation.
As Chris Butler, executive VP at IP Services, says, “Network security isn’t just about firewalls or anti-virus; it’s a layered defense strategy built to anticipate and mitigate risks,”
A comprehensive plan allows businesses to stay resilient amid evolving threats, far more effectively than reactive measures alone.
This blog will explore the steps for creating a strong network security plan, with insights on implementation, real-world examples, and best practices for proactive security. Let’s dive into building a defense strategy that keeps your business secure.
Core Types of Network Security Protections Every Business Needs
1. Why Network Security Is No Longer Optional
In today’s digital landscape, a network security plan isn’t just a safeguard; it’s a strategic necessity.
Cybercriminals constantly exploit vulnerabilities, with many targeting weak, unprotected systems. Small to medium-sized businesses are especially vulnerable, often due to inadequate resources for advanced security measures.
A robust network security strategy provides not only protection but also peace of mind, allowing businesses to focus on growth rather than threats. As digital dependency grows, so does the need for a plan that can defend against modern, increasingly sophisticated cyber-attacks.
2. The Real Cost of Neglecting Network Security
The impact of a security breach is often far-reaching, affecting both finances and reputation.In fact, 72% of companies that have experienced a data breach attribute it to insecure Wi-Fi connections.
This stat underscores a serious oversight—one weak link, such as Wi-Fi, can compromise an entire network. Without a security plan, businesses risk hefty losses, potential legal ramifications, and eroded customer trust.
Network security doesn’t just mitigate these risks; it proactively safeguards against them, emphasizing the need to address every vulnerability.
3. Aligning Network Security with Business Goals
A powerful network security strategy should align closely with overall business objectives. Security isn’t about creating barriers; it’s about enabling safe, seamless operations that help a business flourish.
With a reliable network in place, businesses can scale, adopt new technologies, and respond to market demands without hesitation. Leaders often see security as a foundation for innovation, enabling new services and more efficient operations.
This is especially true given that 40% of executives agree that improving network operations would allow them to launch new services effectively, highlighting the symbiotic relationship between network strength and business agility.
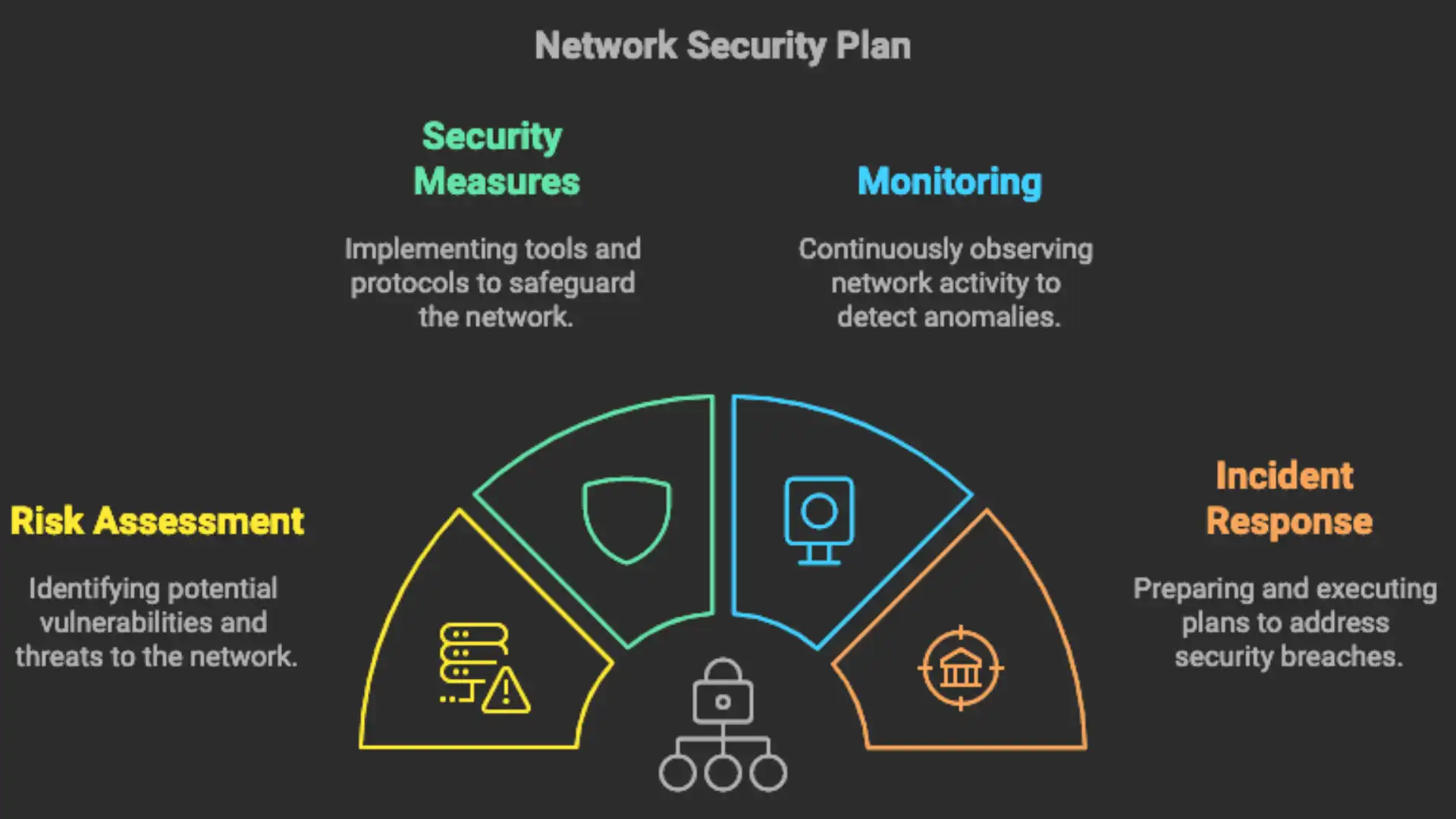
Step-by-Step Guide to Building a Resilient Network Security Plan
1. Risk Assessment and Continuous Audits
Begin by identifying vulnerabilities through a comprehensive risk assessment, highlighting areas susceptible to external and internal threats. Conduct regular audits to keep the network secure against evolving cyber risks and prioritize actions based on potential impact. This forms the foundation of your security plan, allowing timely adjustments to your defensive measures.
2. Implementing Core Security Measures
After assessing risks, implement essential security components like firewalls, Intrusion Prevention Systems (IPS), and network segmentation. Configure these tools based on current threat intelligence and update them routinely to address new risks.
Secure Wi-Fi with protocols like WPA3 and encryption of data in transit and at rest further strengthens your network’s defenses.
3. Access Control and Multi-Factor Authentication (MFA)
Control access to sensitive areas through role-based permissions and enforce the principle of least privilege. Multi-factor authentication (MFA) should be mandatory for critical systems, adding an extra layer of verification against unauthorized access attempts.
4. Employee Security Awareness Training
Since human error poses a significant risk, 95%, as per research, empower employees with regular training on recognizing potential security threats like phishing and social engineering. Security awareness training and testing simulations turn employees into active defenders of network security, building a culture of vigilance.
Incorporating Key Security Tools
The following tools play a significant role in strengthening each step of the security plan. Selecting and implementing the right combination of these tools enables comprehensive protection tailored to address your organization’s unique needs:
|
Security Tool |
Primary Function |
Benefits |
|
Security Operations Center (SOC) |
Centralized monitoring and management of security events |
Provides continuous threat monitoring, incident response, and rapid threat resolution. |
|
Network Access Control (NAC) |
Controls device access to the network |
Ensures only authorized devices and users can connect, reducing unauthorized access risks. |
|
Endpoint Detection and Response (EDR) |
Monitors and responds to threats on endpoints |
Detects, analyzes, and mitigates endpoint threats, enhancing endpoint security across devices. |
|
Data Loss Prevention (DLP) |
Prevents unauthorized data transfers or leaks |
Protects sensitive data by enforcing policies to avoid accidental or intentional data leakage. |
|
Advanced Threat Protection (ATP) |
Detects and defends against sophisticated cyber threats |
Identifies, blocks, and remediates advanced threats like ransomware, enhancing proactive security. |
|
Virtual Private Network (VPN) |
Secures remote access to network resources |
Encrypts data transmitted between remote users and the network, improving remote access security. |
5. Real-Time Threat Monitoring and Incident Response
Use Security Information and Event Management (SIEM) tools for real-time monitoring to detect suspicious activity as it happens. Establish an incident response plan to respond quickly and contain threats before they escalate, reducing potential damage and downtime.
6. Backup and Disaster Recovery Planning
Regularly back up data to secure offsite locations, ensuring rapid restoration in the event of a breach or disaster. Test disaster recovery protocols to confirm they meet recovery objectives, minimizing both data loss and downtime.
| More articles you might like: |
7. Cloud Security and Configuration Management
As cloud adoption grows, enforce strict Identity and Access Management (IAM) policies, encrypt cloud-stored data, and conduct ongoing configuration reviews. Align configurations with industry security standards to protect against unauthorized access, ensuring cloud environments remain secure and resilient.
Upgrade Your Security with a Partner Who Understands Your Needs
In a digital landscape where threats evolve daily, we don’t just offer a standard security solution—we craft a fortified, multi-layered defense uniquely tailored to your business. With deep expertise in proactive threat management and real-time response, our team anticipates vulnerabilities before they become liabilities, creating a security plan that’s both robust and adaptable.
Let’s take your network security to the next level. Contact us to partner with a team that’s as dedicated to your success as you are.


