
Cybersecurity Assessment Checklist to Strengthen Your IT Defenses
How a Cybersecurity Assessment Checklist Builds a Safer IT Environment
Besides the damage of downtime, cyber attacks dismantle trust, halt operations, and expose sensitive data. According to IBM’s 2025 Cost of a Data Breach Report, the global average cost of a cyber incident sits at $4.44 million. Every unpatched system, misconfigured access point, or neglected update widens the path for exploitation.
Most businesses realize this only after the damage is done. Chris Butler, executive VP at IP Services, says
“True security begins with visibility. If you can’t see the risks, you can’t protect against them.”
This blog helps you bridge that visibility gap.
You’ll discover how a cybersecurity assessment checklist empowers you to:
-
Identify hidden vulnerabilities
-
Test your team’s readiness
-
Build consistent defense routines that evolve with the threat landscape
By the end, you’ll understand why visibility isn’t optional and how a simple checklist can be your first step toward lasting resilience.
|
Build Security That Never Blinks! Turn your cybersecurity checklist into a real defense strategy. Partner with IP Services to identify gaps, close them fast, and stay audit-ready. |
What Is a Cybersecurity Assessment Checklist and Why You Need One
A cybersecurity assessment checklist is a structured framework for examining every layer of protection in your IT ecosystem. It helps you identify blind spots before they become breaches.
This checklist helps you:
-
Uncover weaknesses across networks, devices, and user practices
Maintain compliance with evolving regulations
-
Defend against real-world threats
-
Hold your team accountable for a security-first culture
For small and midsize businesses, it’s a practical roadmap that replaces uncertainty with measurable progress. When you review your systems consistently, you gain clarity on:
-
What’s working
-
What’s vulnerable
-
What needs attention next
That’s how you turn cybersecurity from a reactive cost center into a proactive business strength.
Key Areas Covered in a Cybersecurity Risk Assessment Checklist
Your cybersecurity risk assessment checklist should cover every touchpoint where your systems interact with users, vendors, or the internet. Neglecting any of these areas leaves your environment open to attack.
1. Network & Infrastructure Security
Your network is the backbone of business connectivity and often the first target for exploitation.
A single misconfigured router or outdated firewall rule can create invisible entry points for attackers. This is why a strong baseline of protection begins with continuous visibility into your network’s performance and traffic behavior.
Secure it through:
-
Firewall reviews
-
Router and switch configurations
-
Intrusion detection and prevention systems (IDS/IPS)
2. Endpoint & Mobile Device Protection
Every connected device, including laptops, smartphones, and IoT devices, expands your attack surface. As hybrid work becomes the norm, endpoints are now the most frequent targets of malware and ransomware.
A robust endpoint protection program safeguards every device that touches your data. Protect endpoints with:
-
Strong antivirus and anti-malware tools
-
Timely patching and updates
-
Mobile Device Management (MDM) policies for remote hardware
3. User Identity & Access Management
Unauthorized access remains a top cause of compromise, often stemming from password reuse or over-privileged accounts.
Managing user identities is more than authentication; it’s about defining digital trust. Strengthen identity controls by:
-
Enforcing role-based access
-
Enabling multifactor authentication (MFA)
-
Reviewing permissions quarterly to eliminate excess access
4. Cloud & Application Security
Cloud adoption boosts agility but introduces shared responsibility. Providers secure the platform, while you must secure configurations, data, and user access. Without proper oversight, misconfigurations can expose sensitive information.
-
Secure your cloud and apps by:
-
Evaluating configurations
-
Deploying monitoring tools
-
Encrypting data in transit and at rest
5. Vendor & Third-Party Risk
External partners often have access to systems or data that make them indirect extensions of your environment.
A weak vendor can unintentionally introduce threats through the sharing of software or data. Mitigate third-party risks by:
-
Assessing vendor security standards
-
Requesting compliance documentation
-
Defining accountability in contracts
-
Scheduling regular third-party reviews
When each of these areas is actively monitored, you build layers of resilience that work together, rather than relying on a single barrier to stop threats.
Step-by-Step Guide to Building a Cybersecurity Assessment Checklist
Building a cybersecurity checklist doesn’t need to be complicated. What matters is discipline, clarity, and a structure that drives real change.
Here are 7 steps to follow when curating your cybersecurity assessment checklist:
-
Identify Your Digital Assets: Document every device, application, data repository, and external connection. You can’t protect what you don’t know exists.
-
Evaluate Existing Defenses: Review your current tools, including firewalls, antivirus, and backup systems. Do they still align with your business needs and today’s threat landscape?
-
Review Security Policies: Policies must reflect current operations. Outdated guidelines create false confidence and leave gaps in protection.
-
Assess Employee Awareness & Training: According to Infosec, human error is responsible for 74% data breaches. Regular training turns your staff into your first line of defense.
-
Check Compliance Requirements: Regulations like GDPR, HIPAA, and PCI-DSS dictate how you manage sensitive data. Routine compliance checks help mitigate legal and reputational risks.
-
Document & Rank Vulnerabilities: Use scans or penetration tests to uncover weak points. Then categorize findings by severity and likelihood of exploitation.
-
Create a Remediation Plan: Assign timelines, owners, and budgets to each fix. A checklist is only valuable when it leads to measurable action.
This process builds a solid foundation for threat analysis.
|
More articles you might like:
|
How to Use a Threat Assessment Checklist Cybersecurity Experts Recommend
A threat assessment checklist is your early warning system for incoming risks. Cybersecurity experts use it to evaluate both the likelihood of an attack and its potential business impact.
Here’s how to put it to work:
1. Identify Relevant Threats
Start by pinpointing threats specific to your environment. Common risks include:
-
Phishing campaigns
-
Ransomware attacks
-
Insider threats
Each industry faces different challenges, so tailor your checklist accordingly.
2. Assess Impact & Likelihood
For each threat, ask:
-
How easily could this be exploited?
-
What would the damage look like, financial, operational, reputational?
Assign risk levels: low, medium, or high. Use this to guide resource allocation and response planning.
3. Monitor Continuously
Your risk map isn’t static. Track patterns like:
-
Unauthorized logins
-
Unexpected data transfers
-
Configuration changes
Document these shifts to keep your checklist current and actionable.
4. Connect to Business Continuity
A well-used checklist feeds directly into your business continuity and disaster recovery plans. That means faster response times and fewer surprises when something goes wrong.
The Role of Regular Audits in Cybersecurity Risk Assessment
Audits keep your checklist alive. They transform a static document into a dynamic management tool that evolves with your business.
Internal Audits
Conduct quarterly reviews of:
-
System configurations
-
Patch cycles
-
Access logs
These routine checks help catch missteps early and reinforce accountability across teams.
External & Third-Party Audits
MarketsandMarkets™ projects the Managed Security Services market to grow from USD 39.47 billion in 2025 to USD 66.83 billion by 2030, reflecting an 11.1% CAGR over the forecast period.
Businesses are turning to managed security services providers because outside experts bring objectivity and a fresh perspective. They uncover blind spots you may miss internally and elevate your security posture.
Audits provide documented proof of due diligence. Regulators, partners, and insurers want to see that you are proactive.
Track findings. Assign corrective actions. Re-test fixes. This cycle strengthens your defenses naturally and turns audits into a strategic asset.
Integrating Your Cybersecurity Assessment Checklist Into Daily Operations
A checklist only works when it becomes part of your operational rhythm. To avoid it becoming a forgotten document, embed it into the heartbeat of your IT strategy.
1. Make It Routine
Keep security top-of-mind and ensure consistent follow-through. Tie the checklist reviews to:
-
Weekly IT standups
-
Quarterly business reviews
-
Scheduled system maintenance cycles
2. Automate Where Possible
Reduce manual errors by automating:
-
Patch management
-
Backup verification
-
Access log reviews
Automation frees up your team to focus on strategic improvements.
3. Build Accountability
Embed security responsibilities into employee KPIs. When every department owns a piece of the checklist, security becomes a shared priority.
When cybersecurity becomes a routine consideration, your defenses stay consistent, even as your team grows or technology evolves.
Common Mistakes to Avoid in Cybersecurity Risk Assessments
Even the best plans can fail when common pitfalls creep in. Avoid these missteps to keep your assessment process grounded in real outcomes:
1. Treating it as a One-Time Project
Cyber threats evolve daily. Without regular updates, even the strongest checklist quickly becomes outdated
2. Ignoring Insider Risks
Employees, intentionally or accidentally, can expose sensitive data. Combat this with:
-
Ongoing security education
-
Least-privilege access controls
-
Regular behavior monitoring
3. Overlooking Mobile & Cloud Vulnerabilities
Remote work expands your attack surface. Unsecured endpoints and misconfigured cloud systems are prime targets for exploitation.
4. Failing to Act on Findings
Collecting audit data isn’t enough. The checklist’s power lies in execution, not documentation. Assign fixes, track progress, and validate results.
Avoiding these mistakes turns your cybersecurity risk assessment from a paper exercise into a strategic defense tool.
Benefits of a Structured Cybersecurity Assessment Process
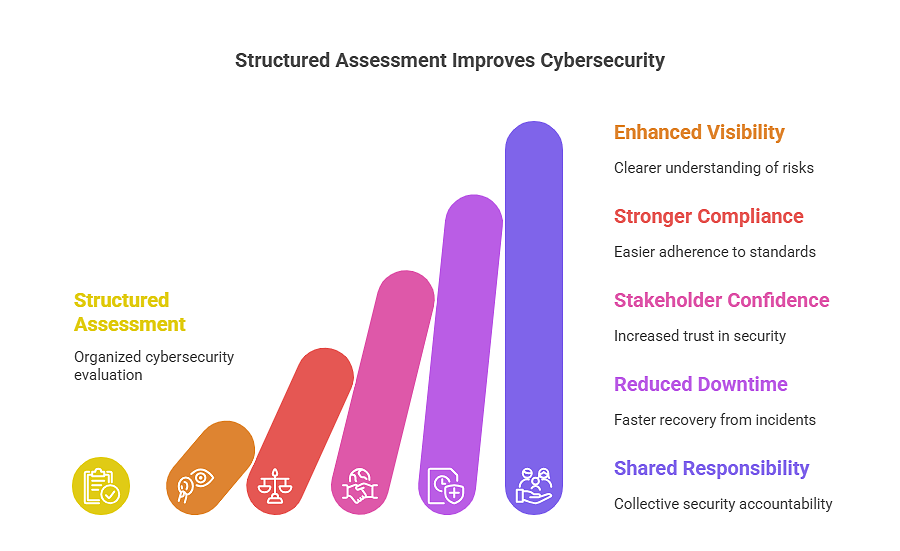 When you follow a structured cybersecurity assessment process, the benefits go far beyond protection.
When you follow a structured cybersecurity assessment process, the benefits go far beyond protection.
-
Enhanced Visibility: You gain clarity across every IT layer, from endpoints to cloud infrastructure, making it easier to spot vulnerabilities before they escalate.
-
Stronger Compliance Alignment: Structured assessments help you stay aligned with regulations like GDPR, HIPAA, and PCI-DSS, reducing legal risk and audit stress.
-
Improved Stakeholder Confidence: When leadership and partners see a disciplined approach to security, trust grows.
-
Reduced Downtime & Recovery Costs: Proactive assessments help you catch issues early, cutting the costs tied to outages, data loss, and emergency remediation.
-
A Culture of Shared Responsibility: Security becomes part of your company’s DNA. When every employee understands their role, your defenses become collaborative and resilient.
How an MSP Can Help With Your Cybersecurity Assessment Checklist
Partnering with a Managed Service Provider (MSP) like IP Services helps you move faster, with greater precision and confidence.
Specialized Tools & Expertise
MSPs bring advanced capabilities for:
-
Continuous monitoring
-
Vulnerability scanning
-
Compliance reporting
They also conduct penetration tests, validate recovery processes, and deliver actionable recommendations aligned with your business goals.
Adaptive & Scalable Support
Since going remote, 80% of businesses have seen threat levels spike, proving flexibility comes with a price tag. MSPs ensure your checklist evolves too, keeping pace with emerging risks and regulatory changes.
Outsourcing to experts saves internal bandwidth. Your team stays focused on core operations while your security posture stays strong. With professional oversight, you gain:
-
Confidence in your defenses
-
Faster response times
-
Improved cyber resilience across the board
Key Metrics to Track for an Effective Cybersecurity Assessment
Tracking progress is often overlooked, yet it’s the key to knowing whether your efforts are paying off. Below is a table highlighting practical metrics you can integrate into your program.
|
Metric |
What It Measures |
Why It Matters |
|---|---|---|
|
Mean Time to Detect (MTTD) |
Average time taken to identify an incident |
Shorter detection time reduces business impact |
|
Patch Compliance Rate |
Percentage of devices with current updates |
Reflects discipline in system maintenance |
|
Backup Verification Frequency |
How often you test data recovery |
Confirms recovery readiness during an attack |
|
Employee Training Completion |
Share of staff trained in cyber hygiene |
Indicates your human firewall strength |
|
Third-Party Audit Findings |
Number of unresolved external audit issues |
Shows transparency and continuous improvement |
Strengthen Your Security with IP Services
A cybersecurity assessment checklist gives your business a clear, repeatable path to stronger protection. It transforms complex IT risks into structured, measurable actions—so you can make informed decisions, maintain compliance, and keep operations uninterrupted.
IP Services leads the way in IT management and cybersecurity, combining technical precision with proven frameworks.
Through our TotalControl™ System, we’ve managed thousands of systems for over 20 years without a single breach, demonstrating unmatched reliability. Our approach, built on best practices from ITIL and Visible Ops, ensures that every client benefits from disciplined processes, high availability, and audit-ready performance.
|
Explore our range of Cybersecurity Services Near You: |
Secure your next move with confidence. Contact us today to schedule your cybersecurity assessment and receive a tailored action plan that strengthens your defenses and drives measurable results.


